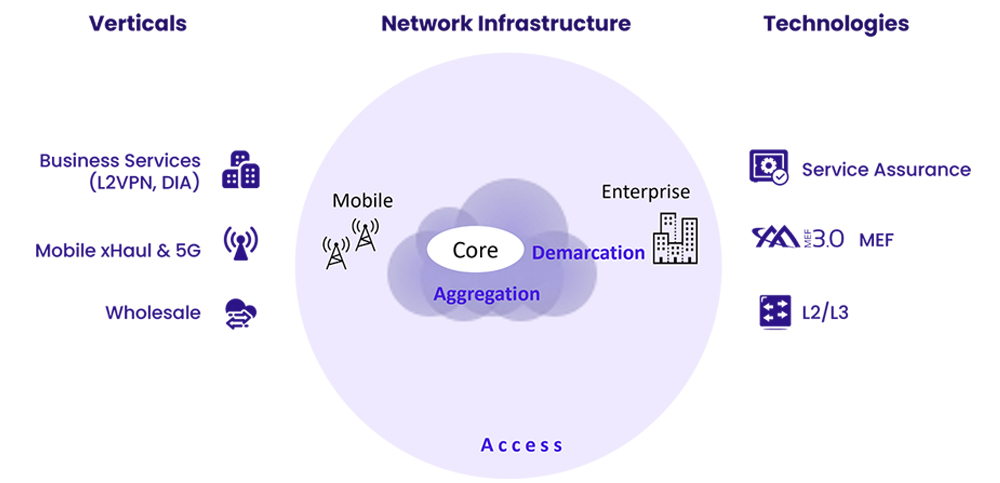
Easily plan, deploy, provision, and maintain SLA-based business services over any access: fiber/copper/TDM/mobile, with Carrier Ethernet access and aggregation supporting rates up to 1/10/25/100G/400G*. Solution for business class access to internet, cloud and VPN services.
Ethernet Access Devices and Routers
Power your network with RAD’s portfolio of network devices and routers for Ethernet access. Our network edge solutions are engineered to help service providers increase revenue and lower costs by deploying reliable, SLA-based services. As a leading supplier of Ethernet switches and network edge devices, we provide robust platforms with zero-touch deployment and powerful traffic management capabilities. Our expertise in Ethernet Layer 2, as well as in combining L2 and L3 capabilities, ensures businesses get the reliable connectivity they need.
Network Edge Switches
A RAD Ethernet access device and router allows service providers to increase their revenues and lower their TCO when deploying SLA-based Carrier Ethernet services with a rich portfolio of service demarcation devices and aggregation platforms.
Also referred to as a carrier ethernet switch or network edge device, RAD’s ethernet network devices and products are MEF CE 3.0 certified and powered by a comprehensive service assured access toolset. These network switches and routers feature such capabilities as:
- Zero-touch deployment and service turn up
- Traffic management
- Timing over packet synchronization
- TDM over Packet
- Performance monitoring, fault management, and resiliency
- Consistent service over fiber, TDM, or DSL
Why Choose RAD for Your Ethernet Access Solutions?
Choosing RAD means tapping into over 40 years of networking leadership and expertise. Our rugged, high-performance gear forms the backbone of complete Ethernet access solutions, empowering you to reduce costs while boosting network performance. As a best-of-breed edge solutions leader with the agility to customize, we meet real-world deployment needs at scale. From advanced L2 Ethernet capabilities to effortless, secure cloud access and AI-powered networking, every product is engineered for tomorrow’s demands. Backed by a global footprint and local expertise, RAD transforms a typical vendor relationship into a partnership built on innovation, customization, and unwavering support.